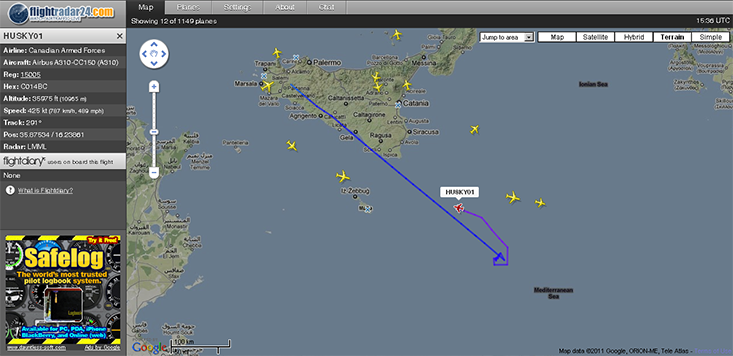
In the run-up to NATO’s 2011 intervention in Libya, a Dutch radio hacker named Huub (@fmcnl) tweeted to the United States military that one of their F-16 fighter jets was mistakenly broadcasting its identity in the clear due to a misconfigured Mode S transponder. When a second fighter plane made the same mistake later that day, Huub joked that Moammar Gadhafi’s radar installations must be down for the U.S. Air Force to be so cavalier with its security protocols: “Hmmm, second fighter showing his ID, a USAF F-15E from 494FS Lakenheath UK, I presume Gadhafis radar equipment has destroyed :o).” Huub was not working alone; he was part of a network of amateurs who were tracking and narrating the chess match in which NATO planes and Libyan units jockeyed for position before the commencement of hostilities. The previous day, Huub had released audio of a U.S. EC-130J psychological warfare plane broadcasting a warning to the Libyan navy (“If you attempt to leave port, you will be attacked and destroyed immediately”). Other volunteers used off-the-shelf websites, such as flightradar24.com and commercial satellite images tagged on Google Earth, to track the movements of military jets, ships, and other potential targets for bombing.
In contrast to the 1990–1991 Gulf War, seemingly a spectacle that the public assimilated passively, the 2011 Libyan war offered a massive dataset for the public to actively sift through on the Internet. As a result, it gave us arguably the first cloud-enabled war. NATO spokesman Mike Bracken described a NATO “fusion centre” that data-mined Twitter feeds and open source databases on the Internet to glean potential targets, battlefield conditions, and other tactical information: “ ‘Snippets of information’ … could then be tested, corroborated or not, by NATO’s own sources, including imagery and eavesdropping from Nimrod spy planes.”1 At the same time, in an interview with the Dutch public broadcaster NOS, the hacker Dirk de Jager also called on listeners to participate in mining these data. Begin with data collection, he said, then sort and analyze the input, and finally the “data puzzle pieces” would fall into place. One might listen, as Huub did, to live air traffic control streams from Malta via liveatc.net and attempt to identify a mysterious plane communicating with the controller—possibly a getaway plane for Gadhafi’s relatives—and correlate that with another stream from Twitter, or to geotag the data’s location in what is known as KML format (see image below). And when the conflict started, the Malta feed even let users anticipate drone strikes by listening for the code “MQ-1,” the designation for Predator drones.
By disrupting the secrecy of NATO’s operations, Huub and de Jager also seemed to counter the regime of state secrecy represented in that respect. Huub’s goal, he wrote, was “to listen to ‘the truth,’ without any military or political propaganda,”2 and de Jager similarly argued that because of the availability of real-time data, state “censorship is no longer possible.” Unsurprisingly, their tweets received a fair degree of criticism for their presumptive interference. One user, @Joe_Taxi, tweeted back to Huub: “If you are not delaying your tweets by a WIDE margin, you are putting the pilots in harms way!!!! … When the sounds of the #operationoddesydawn aircraft are heard in #Libya it should be a complete surprise.” The Guardian helpfully suggested that Gadhafi should start following Huub’s Twitter feed to gain advance warning of each attack. Reflecting back on Huub’s tweets, USAF Captain Jeff Gilmore wrote in the Small Wars Journal: “Accurate tail numbers, routings, home bases for fighters and intercepted propaganda messages by C-130 Commando Solo aircraft are still available on the web for all to hear. It is downright scary to think of our nation’s vulnerabilities from just one overzealous aviation fan.”3
The framing of the Libyan war as a big data problem was itself laden with ideology.
While Huub and his fellow hacktivists seemed to suggest a new avenue for countering state “propaganda,” the results were far murkier. After all, Huub’s leak of the audio from NATO psychological operations was itself a way of disseminating NATO propaganda. And a casual observer might have interpreted a tweet from @hms_cumberland linking to Huub’s clip as a statement of direct support by NATO.4 This was not a statement from the British warship HMS Cumberland, as might have been assumed; @hms_cumberland was, in fact, an unofficial account. Though this tweet was merely an act of a military enthusiast, the confusion inadvertently revealed a cozy relationship between several hacktivists and NATO forces. (The press assumed several of these ‘unofficial’ accounts were fronts for NATO, and at least one French naval officer had indeed set up an unofficial Twitter account for gathering tactical information.5) And Huub’s tweet, for its part, gathered as much praise as criticism from the military community. As military blogger David Cenciotti commented approvingly, Huub’s tweets exposing the NATO planes’ security flaws exemplified “what can be done with off-the-shelf products and a bit of knowledge … skilled enthusiasts following air operations can help the coalition to improve self-protection and safety of some of its High Value assets.”6
The relationship between an avowedly pro-NATO blogger, such as Cenciotti, and the enthusiasts that he cites with approval is complex. As the war progressed, some enthusiasts began to explicitly feed targets to NATO: The Guardian profiled the contributions of one such hacktivist, “a 48-year-old shift supervisor at Dairy Queen ice cream parlour in Tucson, Arizona,” who sifted through satellite photography to tweet coordinates of a suspected Gadhafi communication headquarters to @Nato and @NatoPress; 10 hours after that tweet, he noted proudly, NATO had bombed those exact coordinates.7 Other hackers may be apolitical or passionately opposed to military action, and may look upon such amateur targeters with abhorrence.8 But regardless of what any particular hacker group supported or opposed, the very framing of the Libyan war as a big data problem was itself laden with ideology.
Some of the more evident reasons that hacktivists and government spies have more in common than they would admit lie in the practices shared by both. State and nonstate actors alike use open source tools for a variety of goals, undermining any claim that certain technologies are inherently liberatory or destructive. For example, cypherpunks typically promote the TOR system to counter NSA surveillance. But TOR, a system for accessing the Internet anonymously through encryption and “onion routing,” was originally funded and designed by another branch of the U.S. military, the Naval Research Laboratory (NRL). And as Mike Reed, one of TOR’s original programmers at the NRL, relates, TOR was developed to anonymize the government’s own secret communications and intelligence gathering operations by hiding it within the flow of civilian TOR traffic: The more hacktivist traffic, the better for the government’s intelligence agencies.9 Reasoning that an anonymous backchannel such as TOR has a higher rate of illicit traffic than public Internet browsing, the NSA has even used searches for TOR as a way of targeting potential suspects, and embedded a security hole in TOR browser plug-ins to track users accessing child pornography, leading many cypherpunks to describe TOR as a “NSA honeypot” (i.e., trap). Using TOR may successfully encrypt an individual user’s network traffic, but it does little to solve the larger political problem of state surveillance.
Hacktivists seek to establish a parallel and alternate ecology of media that is supposedly less prone to manipulation or censorship.
In a very practical sense, hacktivism may function as much as a way of furthering putative political causes as vocational training for information workers in a network society. And the military community itself recognizes this: In 2012, for example, NSA director General Keith Alexander recruited hackers at the DEF CON hacker conference by delivering a keynote on the “shared values” held by the intelligence and the hacker community.10
Invitations for hacktivist participation are also inextricable from the ideology of the marketplace. Wired, for example, cites Huub’s radio scanner, which “retail[s] for a little more than $500,” as proof that the hobby is affordable for “average folk.”2 Cenciotti’s call for more amateur hackers to join the war effort frames hacking as a hobby that is “simple and cheap,” yet one that protects the military’s “high value assets.” Thus, in this logic, a hobbyist’s $500 is an investment that pays off immensely: If it can keep a plane from being shot down by revealing security errors, it can potentially save the military the $45 million cost of a “high value” F-16. Similarly, NSA director Keith Alexander concluded his DEF CON speech on “shared values” by arguing that hacker participation in Internet security “would help us with our economic growth. This would be huge for our country. And this area that we’re talking about [the technology industry] is the fastest growing area for our nation for the past three decades. Look at what makes up the Dow Industrial, the NASDAQ … That’s what fuels our economy.”11 (Given how closely enmeshed security is with the marketplace, it is little surprise that former U.S. intelligence analysts have ported their software for mapping communications networks to a new but closely-related field: mapping wealthy investor portfolios.12)
Some hackers may object that the freedom they espouse is not an economic one, but a libertarian ideal; as hacker Richard Stallman put it, “You should think of free as in free speech, not free beer.” That Stallman was compelled to distinguish between the two suggests, however, that the twinned definitions of “free” are fundamentally difficult to separate. Anthropologist Gabriella Coleman has shown that this distinction did not even appear in the free/open source software community until the mid-1990s. Many hackers Coleman interviewed for her 2013 study Coding Freedom commented on the considerable slippage between these two terms: One hacker, for example, exclaimed, “The first draw was, I don’t have to pay for this—awesome!” In Coleman’s words, even in saying “free as in speech … there is some sort of free beer always available, too.”13 The neoliberal framework of the cloud purposely confuses economic intimacy with personal intimacy, making free speech resemble free beer. In doing so, the cloud monetizes users through implicit incentives to “use.” Through this system, users are continually asked to engage in ever more online activity; to participate in constructing themselves as autonomous subjects; and even to misread economic incentives (such as free disk space) as personal freedoms.
Seen correctly, a hacktivist’s freedom most closely resembles that of a free laborer who contributes online reviews, forum moderation, and source code. Free laborers volunteer their services out of their love for the game, even as they are aware that their labor generates value for others. Judged in terms of the cost savings they can provide to NATO, then, the RF hackers working in Libya are difficult to separate from the neoliberal consensus that turns to the marketplace for solutions, and continually seeks lower-cost or even “free” alternatives. Yet to volunteer as a hacker—whether indulging in a “simple and cheap” hobby, or using open source software as “free beer”—is to work within a neoliberal system of free labor.
Consider the case of Washington Post investigative reporters Dana Priest and William Arkin, who created the Top Secret America website in 2010. Like other websites that visualize data in the cloud, Top Secret America aggregated massive amounts of data about which private contractors worked for the CIA or NSA, including expenditures and geographical locations. By overlaying a visual interface onto a “Top Secret” world, Top Secret America purported to use appropriations data to understand and even expose a hitherto unrepresentable world. Users could sort by specific weapons technologies (counter-IED explosives operations, for example), search a geocoded map by zip code to find “counterterrorism organizations near you,” and so on, creating a visual interface resembling the hacktivists’ geocoded maps of military units in Libya.
Once again, Top Secret America sparked a debate over secrecy similar to that of Huub’s tweets. Commentators attacked Priest and Arkin’s project as a national security risk, faulting them for disclosing too much information about America’s covert operations. Priest was eventually asked about her motivations: Did she belong to the radical transparency movement, which attempted to subvert NSA surveillance by exposing its secrets? No, she responded; that wasn’t her intention: “The goal is to figure out if the system is working as well as it should and to make it better.” Indeed, the then U.S. Secretary of Defense Robert Gates even praised Top Secret America as a valuable service that could help eliminate redundancies and overpriced contracts from a bloated intelligence budget. Motivated by the same market ideologies—the idea of efficient markets and economic, rather than legal, rules—that undergird the mechanism of security in the contemporary West, the do-it-yourself tactics of participatory media are a perfect match for the surveillance state: Any citizen, it says, can engage with his or her security regime by exercising surveillance over budgets and other tasks of management.
What is most interesting here is the critics’ confusion: A project that attempts to aid the government in its secret program of surveillance is indistinguishable from projects that aim to undermine the government’s surveillance programs. Confusing the two types of projects is, however, an easy mistake to make: Top Secret America’s interface visually resembles those of oppositional websites, such as The Guardian’s map of Iraq war casualties. Indeed, the link-node interface, the graphs, and the toolbars to filter and sort data are so common that they have become naturalized in an age of big data; these interfaces are as inseparable from large datasets as Renaissance perspective is from photographic images. These data interfaces came out of a distrust for normative media representations (talking heads on TV, the “NATO propaganda” at press conferences, potentially Photoshopped satellite images of Iraq, and so on). When the hacker collective Anonymous retweeted an article about Huub’s link, asking: “Want unfiltered information (aka the truth) on the bombings in Libya? Read http://bit.ly/ftZpWx and follow @FMCNL #libya #UN,” we recognize the implication that big data gives citizens unmediated access to “the truth.” Portraying themselves as iconoclasts—literally, destroyers of icons or images—hacktivists seek to establish a parallel and alternate ecology of media that is supposedly less prone to manipulation or censorship. If any given image can be duplicitous, the only way to find the truth—so goes de Jager’s claim—is to correlate and situate that image within a network of other images, to look through its duplicitous surface and decode and decrypt the hidden network within the network.
A hacktivist project to undermine the government looks like a security project meant to bolster the government. Huub’s attempt to counter the “propaganda” of the state simultaneously provides the state with feedback on how its operations are functioning. The attempts to expose or unmask the mechanism of power in fact only succeed in preserving its underlying logic.
Tung-Hui Hu, a former network engineer, is an assistant professor of English at the University of Michigan and the recipient of a 2015 NEA literature fellowship.
Reprinted with permission from A Prehistory of the Cloud by Tung-Hui Hu, published by the MIT Press. All rights reserved.
References
1. Norton-Taylor, R. & Hopkins, N. Libya air strikes: Nato uses Twitter to help gather targets. The Guardian (2011).
2. Schachtman, N. Listen: Secret Libyan psyops, caught by online sleuths. Wired (2011).
3. Gilmore, J. Where Is Lt Zuckerberg? Small Wars Journal (2013).
4. Audio of USAF aircraft on HF radio warning a Libyan ship to stay in port or be attacked & destroyed. https://t.co/5lEOoyQ (2011).
5. Pollock, J. People power 2.0. MIT Technology Review (2012).
6. Cenciotti, D. Operation Odyssey Dawn explained (day 3). The Aviationist (2011).
7. Gabbatt, A. Nato, Twitter, and Air strikes in Libya. The Guardian (2011).
8. Coleman, E.G. & Golub, A. Hacker practice. Anthropological Theory 8, 255-277 (2008).
9. Reed, M. TOR made for USG open source spying. Cryptome (2011). https://cryptome.org/0003/tor-spy.htm
10. Kopfstein, J. How the NSA recruits in a post-Snowden world. The Daily Beast (2014).
11. Alexander, K.B. DEF CON 20 by General Keith B Alexander Shared Values Shared Response. https://www.youtube.com/watch?v=Rm5cT-SFoOg (2013).
12. Hardy, Q. Wealth Managers Enlist Spy Tools to Map Portfolios. The New York Times (2014).
13. Coleman, E.G. Coding Freedom Princeton University Press, Princeton, NJ (2012).